Cueing up a calculator: an introduction to exploit development on
4.6 (173) · € 18.00 · En Stock
Using CVE-2023-43641 as an example, I’ll explain how to develop an exploit for a memory corruption vulnerability on Linux. The exploit has to bypass several mitigations to achieve code execution.
Frontiers Visual Analytics for Operation-Level Construction Monitoring and Documentation: State-of-the-Art Technologies, Research Challenges, and Future Directions

198269823 metasploit the penetration testers guide by M4st3rm1nd - Issuu

Oege de Moor (@oegerikus) / X

Scientific calculator project in c language

Cued reaction time task. Between a preparation cue and response cue, a

PentesterLab on LinkedIn: PentesterLab: White Badge

kmkz (@kmkz_security) / X

Deliverable D 4.1: MAPPING REPORT FOR CZECH REPUBLIC
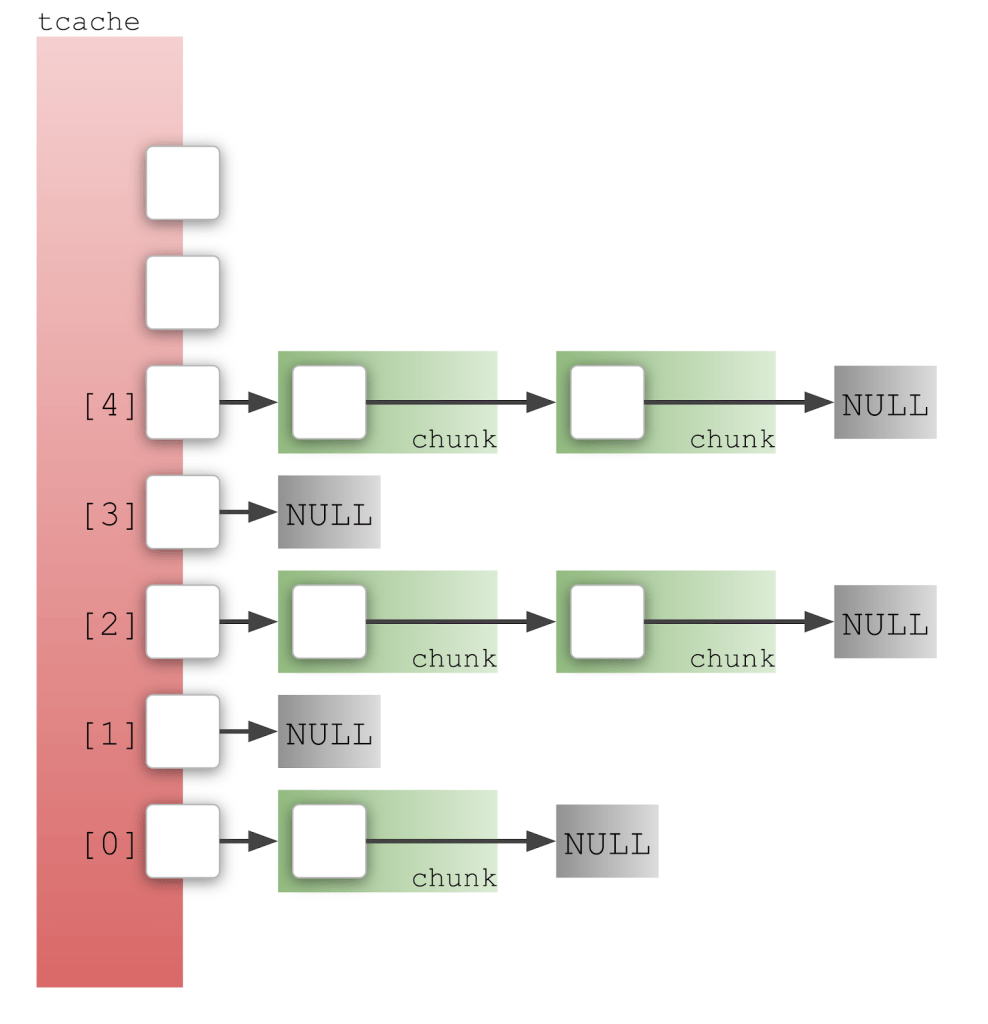
Cueing up a calculator: an introduction to exploit development on Linux - The GitHub Blog

Scientific calculator project in c language












